How to evaluate data platform security: 5 criteria that actually matter
.png)
.png)
Table of Contents
TL; DR
- Data platform security is about control, not just encryption or compliance checkboxes
- Most organizations unknowingly trust platforms they don’t fully understand or audit
- Evaluating security protects sensitive data from breaches
- Strong security frameworks ensure regulatory compliance and reduce legal risk
- Application security protects software
- Data platforms face higher risk due to constant movement through ETL, pipelines, and integrations. Ensuring data platform security protects business-critical data itself
- Separation of control and data planes is a core indicator of secure architecture
- Zero trust, auditability, and fine-grained access control are non-negotiables
- True data security for enterprises focuses on where your data lives, who accesses it, and how it moves across systems
Data is now the backbone of every decision, every forecast, and every strategic move. Yet most organizations still trust platforms they barely understand and assume that security is “handled” because they checked a few compliance boxes or enabled encryption to keep hackers away.
But data platform security isn’t just about keeping hackers out. It’s about control. Who can access your data? Where does it actually live? How does it move across systems? And when something goes wrong, do you really know what’s happening, or are you just hoping for the best?
Read this guide to understand what data platform security means and explore the five security criteria that you should consider when you evaluate a data platform.
What does data platform security mean?
Data platform security is a commitment to protecting the data that powers your business wherever it lives, however it moves, and no matter who touches it.
Based on standard definitions, it means giving the right people and processes access while keeping everyone else out, maintaining data accuracy and trustworthiness at all times, and making sure that information stays available even during outages, migrations, or infrastructure changes.
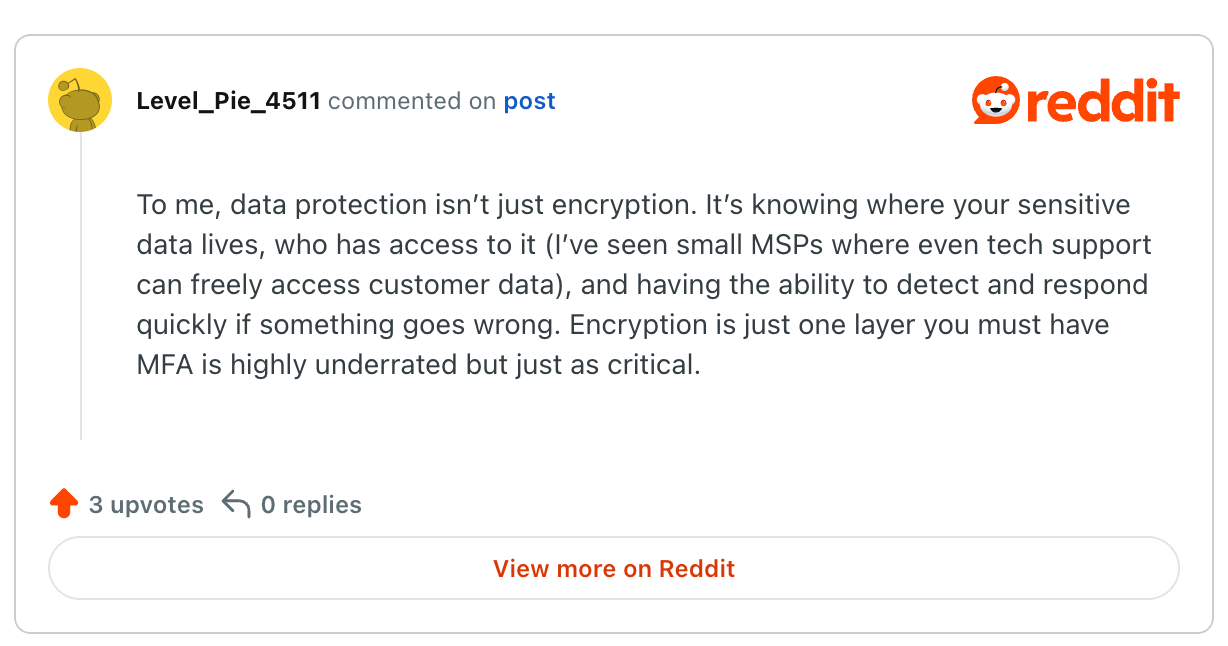
According to participants on a cybersecurity Reddit thread, true data security involves more than just “good compliance” and it goes beyond ensuring encryption or TLS.
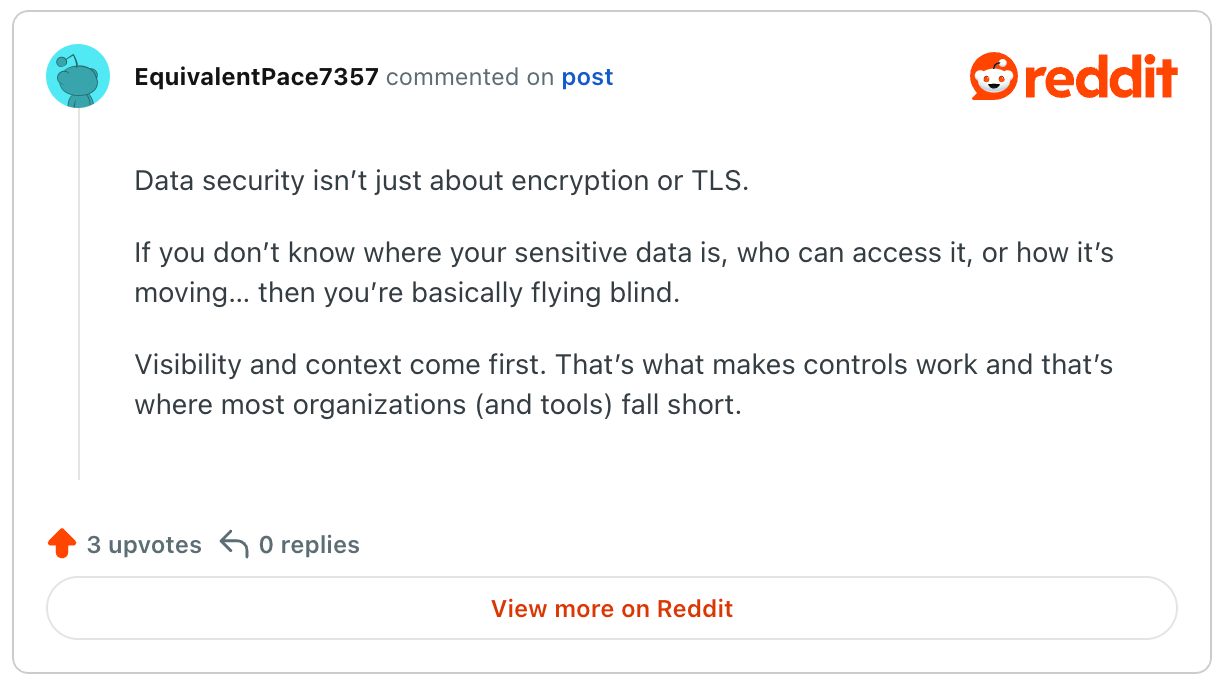
For others, data protection goes beyond ensuring encryption and protecting from cyber threats.
Why is it important to evaluate your data platform’s security?
When your data is safe, trustworthy, and auditable, your team can build on it confidently, scale faster, and make smarter decisions. Here’s why it is important:
- Protects sensitive data & prevents breaches: Your data warehouse or data lake often holds your most sensitive business information such as PII, financial data, customer behaviour, product metrics, etc. A security lapse means that data could be exposed, stolen or corrupted. Beyond immediate financial loss, this erodes trust with customers and partners
- Ensures regulatory compliance: Many industries (finance, healthcare, SaaS) have compliance obligations (GDPR, HIPAA, SOC 2, etc.). A robust data platform must support encryption (both in transit and at rest), role-based access, and auditing. Without evaluating security, you risk non-compliance, which can lead to heavy fines and brand damage
- Reduces risk during data movement and transformation: Data platforms store data while simultaneously moving (ETL/ELT), transforming, and often integrating it with various systems. During migration or syncing, security misconfigurations can create leaks or vulnerabilities. Guarding data during this migration stage is vital because that's when it's most exposed
- Maintains trust and business continuity: If your analytics platform gets compromised, it’s a security incident and a business disruption. Teams reliant on BI or machine-learning pipelines stop trusting the data. Building strong controls ensures lineage, ownership, and recovery mechanisms, so your data is reliable and actionable
- Enables secure scaling and innovation: As you scale your data infrastructure, you’ll probably add more sources, more users, and more tools. Without strong foundational security, complexity grows faster than control. By evaluating how the platform isolates workloads, enforces least privilege, and supports robust identity management (core criteria from Fivetran), you future-proof your data stack
What makes data platform security different from application security?
Unlike application security, which focuses on protecting code and runtime, data platform security ensures that the heart of your business i.e. your data remains private, reliable, and compliant.
Here’s a breakdown of how security differs for both:
In short, application security protects how your software runs. Data platform security protects what runs your business, i.e. the data itself. And that’s why it demands deeper control, stricter governance, and structural security, not just surface-level protection.
Five non-negotiables for evaluating data platform security
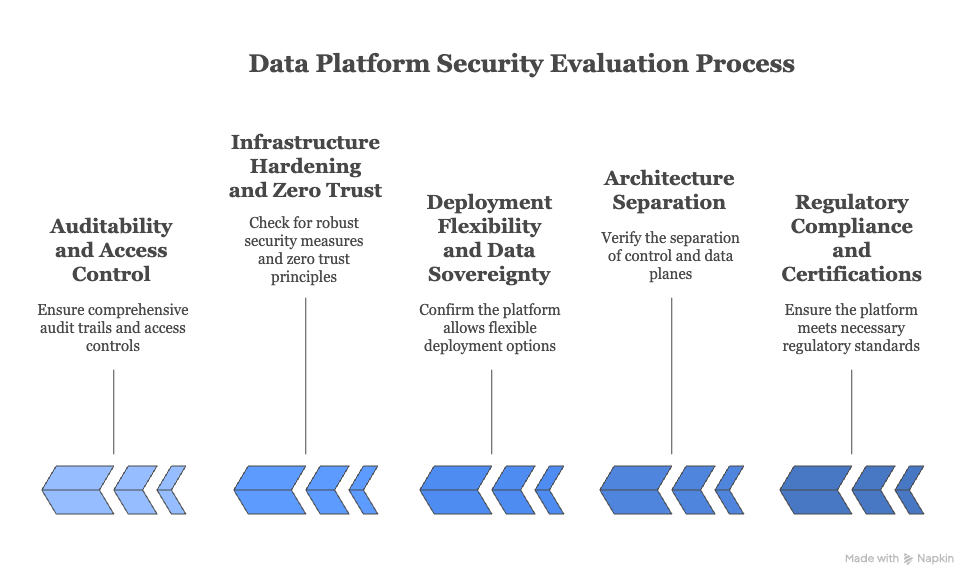
When you’re assessing the security of a data platform, it’s not about ticking technical boxes. It’s about asking one critical question: Can I trust this platform with my data?
Here are the five fundamentals you should not compromise on.
1. Regulatory compliance and certifications
Security starts with compliance. If a platform can’t help you meet regulatory obligations, it automatically becomes a risk, not a solution. Frameworks like GDPR, HIPAA, and SOC 2 are indicators of operational maturity and trustworthiness.
Look for platforms that demonstrate compliance through independent audits, detailed documentation, and transparent security processes. This gives your leadership, legal, and compliance teams confidence that the platform won’t become a liability during audits or regulatory reviews.
Certifications like SOC 2 Type II, HIPAA compliance, and alignment with GDPR and CCPA show that security is baked into the architecture, processes, and day-to-day operations, making enterprise adoption far smoother and safer.
2. Architecture that separates control from data
True security begins at the architectural level. One of the most important indicators of a secure data platform is a clear separation between the control plane and the data plane.
This separation ensures that data movement stays isolated and protected, while orchestration and monitoring happen through a separate management layer. It limits exposure, reduces attack surfaces, and prevents unnecessary access to sensitive data.
3. Deployment flexibility and data sovereignty
Security means control over where your data lives and how it’s processed. A reliable platform should allow flexibility across public cloud, private environments, or fully self-managed deployments.
For organizations with strict data residency requirements, the ability to run data pipelines inside their own infrastructure is essential. Estuary Flow offers public, private, and BYOC models, allowing businesses to maintain sovereignty without sacrificing performance or functionality.
This flexibility ensures compliance, reduces latency, and removes unnecessary data exposure risks.
4. Infrastructure hardening and zero trust principles
Security is as much about minimizing internal risk as it is about external threats. Zero trust architecture ensures every request is verified, validated, and authenticated.
Look for platforms that invest in hardened infrastructure, immutable systems, and encrypted internal communication. This minimizes the risk of lateral breaches and internal vulnerabilities.
Implementing hardened operating systems, mutual TLS authentication, and scoped access tokens, reduces both internal and external threat surfaces significantly.
5. Auditability and access control
Security is about creating accountability and monitoring who accessed what, when, and why.
A secure data platform provides clear audit trails, role-based access control, token-based authentication, and complete visibility into actions across environments.
Ensure that all access is logged, traceable, and governed through structured role controls to make audits, reviews, and compliance reporting significantly easier and more reliable.
5X delivers enterprise-grade security across your data lifecycle
A secure data platform isn’t just about encryption or ticking compliance checkboxes. It’s about having complete control, deep visibility, and consistent governance across every stage of your data lifecycle from ingestion to transformation, access, analytics, and AI. This is exactly where 5X positions itself as the platform of choice for security-first organizations that can’t afford compromise.
5X is engineered for enterprises that handle sensitive, high-impact data at scale. Its architecture ensures strict separation between the control plane and data plane, meaning orchestration and monitoring never expose or interfere with your actual datasets. This design minimizes attack surfaces, enforces isolation by default, and protects data even as it moves across pipelines, warehouses, BI tools, and AI systems.
5X also enables granular role-based access control, ensuring that every user, team, and system has access only to what they absolutely need, nothing more. Sensitive data is protected through PII-safe architecture, giving organizations the ability to classify, control, and monitor data usage without slowing down analytics or operational workflows.
The platform also balances security and speed efficiently. Teams get real-time insights, AI-ready data infrastructure, and scalable analytics, all without introducing risk or complexity. Instead of layering security onto fragmented systems, 5X embeds it into the core of your data stack.
FAQs
What is the most important security feature in a data platform?

How do I verify a data platform’s compliance certifications?

What security questions should I ask during a data platform demo?

How does data sovereignty impact platform security decisions?

Why is zero trust critical for modern data platforms?

How does auditability strengthen enterprise data security?

Building a data platform doesn’t have to be hectic. Spending over four months and 20% dev time just to set up your data platform is ridiculous. Make 5X your data partner with faster setups, lower upfront costs, and 0% dev time. Let your data engineering team focus on actioning insights, not building infrastructure ;)
Book a free consultationHere are some next steps you can take:
- Want to see it in action? Request a free demo.
- Want more guidance on using Preset via 5X? Explore our Help Docs.
- Ready to consolidate your data pipeline? Chat with us now.

How retail leaders unlock hidden profits and 10% margins
Retailers are sitting on untapped profit opportunities—through pricing, inventory, and procurement. Find out how to uncover these hidden gains in our free webinar.
Save your spot






%201.svg)

.png)






